|
|
|
|||||||||||||||||||||||||||||||||||||||
RHUB Web Conferencing Security |
The weakest security point in web conferencing |
Web conferencing is an Internet based application. For any Internet
application, there must be two types of security measures that
work together to ensure the adequate security:
For web conferencing applications, transmission security can be easily met since every system has its own proprietary data format and protocol, which are very hard to decode by hackers. In addition, the data transferred is made up of screen pixels, not document files. That is why most of the top web conferencing vendors do not use a strong encryption algorithm such as SSL to encrypt the image data in order to avoid performance penalty. The weakest security point in web conferencing is the access security. Every web conferencing system today uses meeting ID and/or password as a simple access security measure to protect unwanted attendance. However, the problem is that the meeting ID/password is usually emailed to attendees before scheduled meetings start. This process can easily comprise the access security. Once a hacker gets/guesses your meeting ID/password, your meeting screen is captured in seconds by the unwanted attendance. It would be too late to close your meeting once you find such hacking. Access security is the biggest security issue to all hosted web conferencing services. Some leading hosted service providers proudly claim they have the best security simply because they have deployed the industry standard encryption protocols such as SSL and AES. This type of security measure only slightly contributes to the transmission security. |
Deploy RHUB web conferencing appliance for the best security |
|
The best way to resolve access security issues described
above is to use an on-premise solution in order for your firewall to protect
your meetings. RHUB web conferencing appliance is the best and easiest
as well as the most
affordable on-premise solution.
The figures below show three typical ways to deploy RHUB web conferencing appliance:
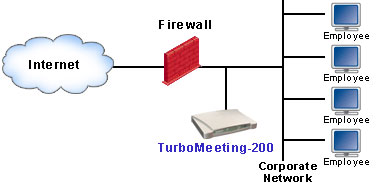
(a) Behind Firewall Deployment
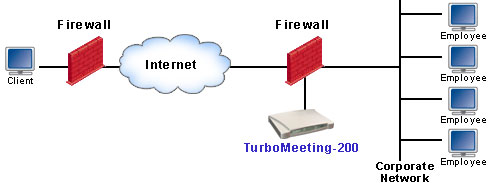
(b) DMZ Deployment
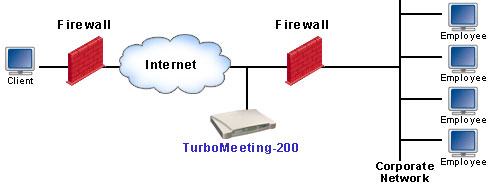
(c) Outside Firewall Deployment Both behind-firewall and DMZ deployment achieve the access security purpose. Today DMZ is available for almost every router including home routers. DMZ deployment provides the most flexibility. It allows both internal (behind firewall) and external (outside firewall) attendees join a meeting. When you start a meeting, you simply check an option to tell the system that this meeting is for internal attendees only. RHUB web conferencing appliance will reject any attendees who come from outside your firewall. The outside-firewall deployment is equivalent to hosted services. It does not add anything to the access security, but weakens it. |
|
||